this post was submitted on 06 Oct 2024
728 points (91.0% liked)
Technology
58550 readers
6744 users here now
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related content.
- Be excellent to each another!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, to ask if your bot can be added please contact us.
- Check for duplicates before posting, duplicates may be removed
Approved Bots
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
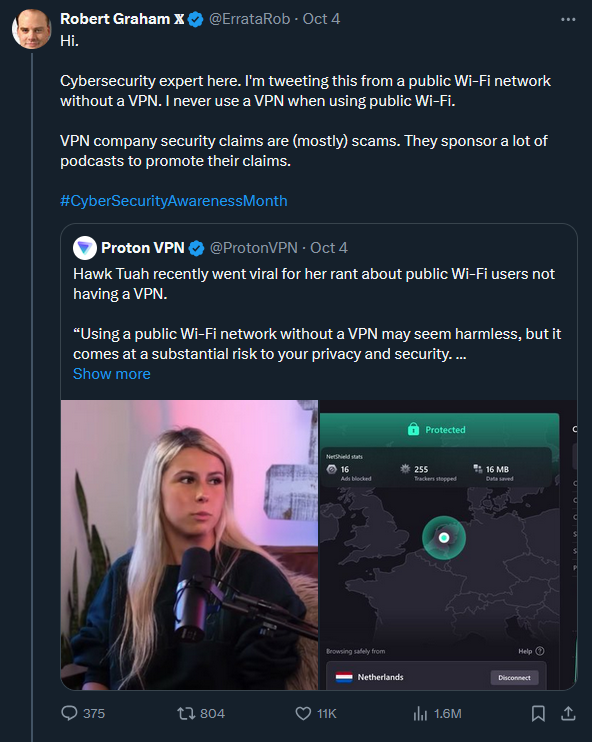
What is he talking about, public WiFi can easily poison and monitor your DNS requests (most people don't know or use encrypted DNS), and there's still tons of non-https traffic leaks all over the place that are plain text. Even if encrypted, there's still deep packet inspection. VPNs can mitigate DPI techniques and shift the trust from an easily snoopable public WiFi to the VPN's more trustworthy exit servers.
This guy really needs to elaborate on what he's trying to say when the cyber security field very much disagrees with this stance. I'm not a huge fan of Proton, but they aren't doing anything wrong here. You should use it for public Wi-Fi.
How is DPI a problem if it's encrypted? That would only work if the attacker had installed their CA cert on your client machine, right?
I think it might be confusion between inspecting plaintext metadata like SNI vs actually inspecting encrypted contents (e.g. HTTPS content, headers, etc.).